Stealth Wiegand Data Interpreter
Operating Manual for the PPE Stealth Wiegand Data Interpreter
Introduction
The PPE Stealth Wiegand Data Interpreter (WDI) aims to facilitate a new method of intial access and aid in physical privelege escalation in badged applications (e.g., server room / restricted area access) while employing non-destructive tooling.
What’s included in the box?
When you receive your Stealth Wiegand Data Interpreter, the box will contain the following items:
| Item | Description |
|---|---|
| HID multiClass SE Reader | Supports iCLASS (Legacy)/SE/SEOS (Standard Keys), HID Prox, EM, and AWID |
| PPE Blackplate & Electronics | Mounting platform and electronics |
| PPE Stealth Card | Used for disabling the wireless AP, extending battery life, and improving LF card performance |
| iCLASS 2k Card | Used for writing captured iCLASS/SE/SEOS card data (proxmark3 required) |
| T5577 Card | Used for writing captured HID Prix, EM, and AWID card data (proxmark3 required) |
| Command Strips | Expendable item |
| 9v Lithium Batteries | Expendable item |
| Isopropyl Alcohol | Expendable item |
| Security & Philips Head Screws | Use the provided spanner bit and security screw to aid in use cases where tampering may be a concern |
| Spanner Screwdriver Bit | N/A |
| Hex Key Wrench | N/A |
Battery Recommendations
Why did we choose the 9V platform for the stealth reader? While we assessed just about every battery and voltage type along with boost and buck converters, after traveling through airports and running the device through it’s paces we landed on the 9V as the most suitable candidate for these reasons:
- 9V batteries are readily available anywhere you go and are cost effective
- 9VDC is the perfect voltage for powering both the HF and LF elements within the multiCLASS SE reader (e.g., provides ideal read range)
We have tested the following batteries while running our reader in Stealth Mode:
| Item | Average Run Time | Use Case |
|---|---|---|
| TENERGY 1,200mAh 9V Lithium | 6.5 hours | Live Operations, best performance |
| Standard 9V Alkaline ~500mAh | 2.5 hours | Live operations/testing |
| HW 1,000 mAh 9V Li-ion Rechargeable | 2.5 hours | Testing/live operations. Reader will need to be in Stealth mode to optimize LF reading capabilities |
Getting Started
Opening the Reader
The reader ships fully assesmbled, tested, and ready for operation. To open Stealth, remove the philips head screw at the bottom of the reader and carefully tilt the baseplate up towards the top of the reader as illustrated below.
Powering the device
With the reader open, attach the 9V battery to the holding tray. If needed, use the supplied spanner bit to assist in seating the battery as illustrated below:

To power the reader on, move the slide switch from the OFF to ON position on the Stealth readers breakout board.
Closing the reader
To close the reader, slide the lip of the baseplate under the readers retention lip. Apply slight upward and forward pressure to the baseplate and tilt the baseplate down as illustrated below. Once fully seated lock the baseplate in place using the supplied security screw or philips head screw. Note, do not over tighten the baseplate screw.
Connecting to the Stealth Reader
Use your phone or computer to connect to the Stealth Readers Doppelgänger firmware. Below are the default credentials:
| SSID | Password |
|---|---|
| doppelgänger_XXXX | UndertheRadar |
Once connected, open http://rfid.local/ or http://192.168.4.1/ in your browser. The page is where you find a parsed output of captured cards. Note, only cards that have Wiegand parsers built will show up in this area. Cards like EM, will show up in the CSV File. Just use the HEX or BINARY data, when writing the captured data to a blank card.
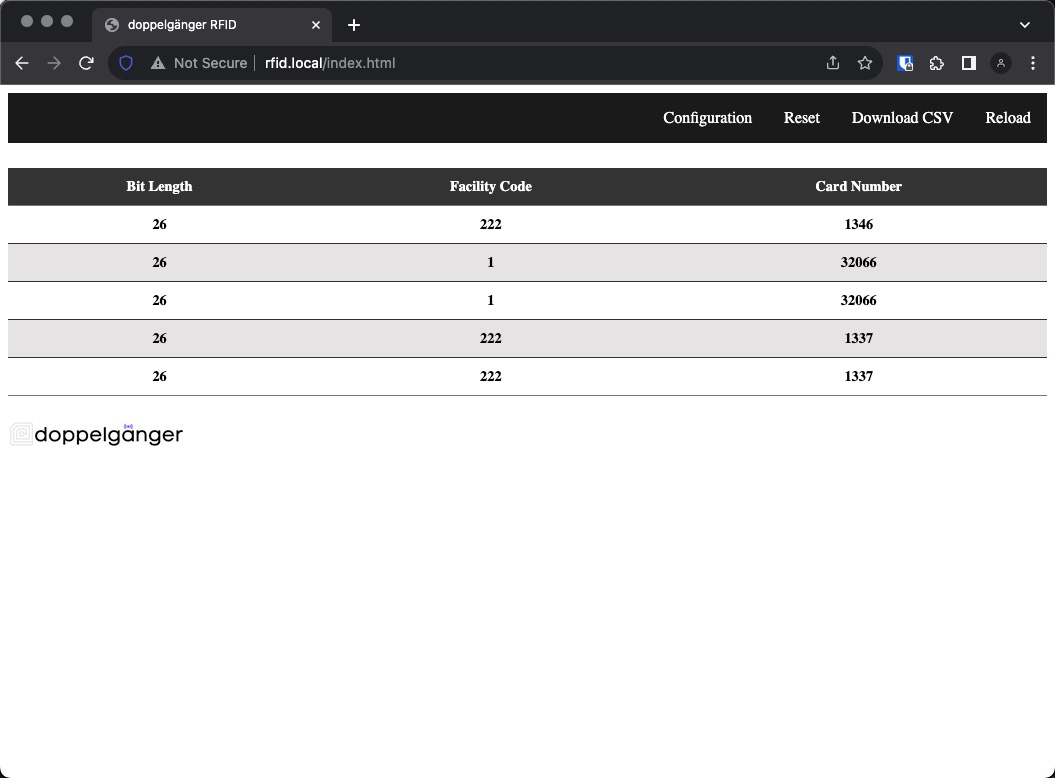
We ship every Stealth Reader with a standard Stealth Card consisting of the following values:
| Bit Length | Facility Code | Card Number |
|---|---|---|
| 26 | 222 | 1337 |
Mounting the Reader
The stealth reader comes with large sized 3M Command Strips for mounting. These strips are rated for 15 lbs and will more than adaquately support the weight of the reader (15 ounces). However, it is absolutely critical to chose the appropriate mounting solution for each unique application.
If you’re using the Command Strips, follow the manufacturer’s guidance below. Do not attempt to mount the reader in wet, damp, or otherwise unstable conditions. Additionallly, do not attempt to mount the reader to any surface that you feel may cause issues upon removal (e.g., paint peel/flaking).
SURFACE PREP: Clean the desired surface with rubbing alcohol to remove grime and dust to allow the wall hangers to bond to the surface; the indoor temperature must be between 50 degrees Fahrenheit and 105 degrees Fahrenheit.
REMOVAL: Lightly hold the top of the wall adhesive strips and slowly pull straight down towards the floor to remove and prevent damage of walls and surfaces.
Customization
You can modify the default wireless credentials and stealth card values from the Configuration page.
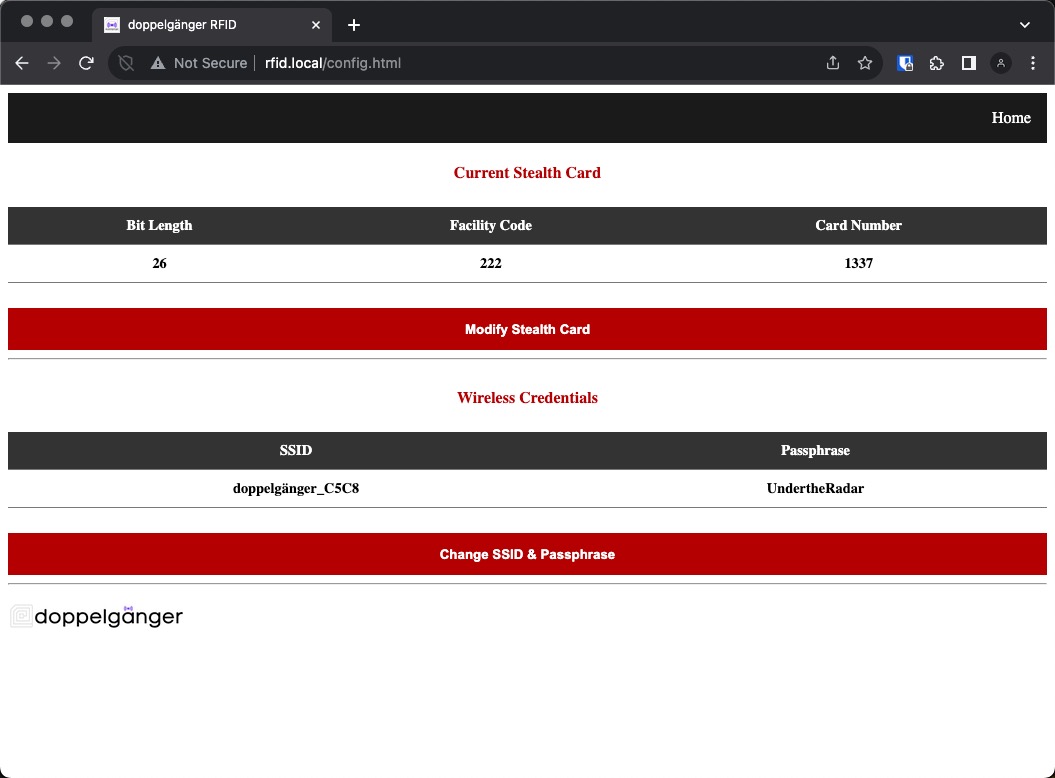
Click on the Modify X option to alter the defaults.
Custom Stealth Card Parameters
Custom Stealth Card values must fall within the specified ranges. We suggest utilizing an HF iCLASS 2k card as your main stealth card. This recommendation is due to the sensitivity of the HF element within the reader, which serves as the primary element on multiCLASS SE readers. As your 9V battery approaches the end of its lifespan, the LF element gradually loses power, necessitating closer card contact with the reader (the secondary/optional read element on multiCLASS SE readers). In contrast, the HF element will maintain an extended read range until the battery is fully depleted.
| Bit Length | Facility Code | Card Number |
|---|---|---|
| 26 or 35 | 1 - 255 | 1 - 65,535 |
Below is an example using the Iceman Fork of the proxmark3 firmware to write a 26-bit and 35-bit stealth card.
# 26-bit Example
[usb] pm3 --> lf hid clone -w H10301 --fc 222 --cn 1337
[=] Preparing to clone HID tag
[+] [H10301 ] HID H10301 26-bit FC: 222 CN: 1337 parity ( ok )
[?] Hint: try `lf hid reader` to verify
[=] Done!
# 35-bit Example
[usb] pm3 --> lf hid clone -w C1k35s --fc 222 --cn 1337
[=] Preparing to clone HID tag
[+] [C1k35s ] HID Corporate 1000 35-bit std FC: 222 CN: 1337 parity ( ok )
[?] Hint: try `lf hid reader` to verify
[=] Done!
The following is an example using the Iceman Fork of the proxmark3 firmware to write a custom iCLASS 2K stealth card. You may also need the this Card Calculator Python Script to assist:
# Grab the Card Calculator
wget https://raw.githubusercontent.com/tweathers-sec/useful_physical_information/main/card_calculator.py
# Usage
python3 card_calculator.py -h
Usage: card_calculator.py <indala || prox || iclass> <FC> <CC> <26 || 35>
# Generating Card Details
python3 card_calculator.py iclass 222 1337 26
Write the following values to disable encryption on the card:
Blk 6 - 030303030003E014
Blk 8 - 0000000000000000
Blk 9 - 0000000000000000
Write the following to Blk 7 on an iClass card:
0000000005bc0a73
Take the output provided by the card calculator and use the write block function to write the data to an iCLASS 2K card.
# Writing the provided data to a iCLASS 2K card
[usb] pm3 --> hf iclass wrbl --blk 6 -d 030303030003E014 --ki 0
[+] Using key[0] AE A6 84 A6 DA B2 32 78
[+] Wrote block 6 / 0x06 ( ok )
[usb] pm3 --> hf iclass wrbl --blk 7 -d 0000000005bc0a73 --ki 0
[+] Using key[0] AE A6 84 A6 DA B2 32 78
[+] Wrote block 7 / 0x07 ( ok )
[usb] pm3 --> hf iclass wrbl --blk 8 -d 0000000000000000 --ki 0
[+] Using key[0] AE A6 84 A6 DA B2 32 78
[+] Wrote block 8 / 0x08 ( ok )
[usb] pm3 --> hf iclass wrbl --blk 9 -d 0000000000000000 --ki 0
[+] Using key[0] AE A6 84 A6 DA B2 32 78
[+] Wrote block 9 / 0x09 ( ok )
To validate the success you can dump the card and decrypt the .bin file.
# Dump the iCLASS card
[usb] pm3 --> hf iclass dump --ki 0
<REDACTED FOR BREVITY>
[+] saving dump file - 19 blocks read
[+] saved 152 bytes to binary file `/Users/tweathers-sec/hf-iclass-91D95902F8FF12E0-dump.bin`
[+] saved to json file `/Users/tweathers-sec/hf-iclass-91D95902F8FF12E0-dump.json`
[?] Try `hf iclass decrypt -f` to decrypt dump file
[?] Try `hf iclass view -f` to view dump file
# Decrypt the data
[usb] pm3 --> hf iclass decrypt -f /Users/tweathers-sec/hf-iclass-91D95902F8FF12E0-dump.json
<REDACTED FOR BREVITY>
[=] Block 7 decoder
[+] Binary..................... 101101111000000101001110011
[=] Wiegand decode
[+] [H10301 ] HID H10301 26-bit FC: 222 CN: 1337 parity ( ok )
[+] [ind26 ] Indala 26-bit FC: 3552 CN: 1337 parity ( ok )
[=] found 2 matching formats
[=] -----------------------------------------------------------------
Custom Wireless Access Point Configuration
When modifying the wireless access point credentials, keep the following parameters in mind. If for whatever reason, you lock yourself out of your stealth reader (e.g., forget your wireless passphrase) - contact the PPE store with the e-mail that you used to purchase your reader.
| SSID | Passphrase |
|---|---|
| No Limitations | 8 - 24 Characters |
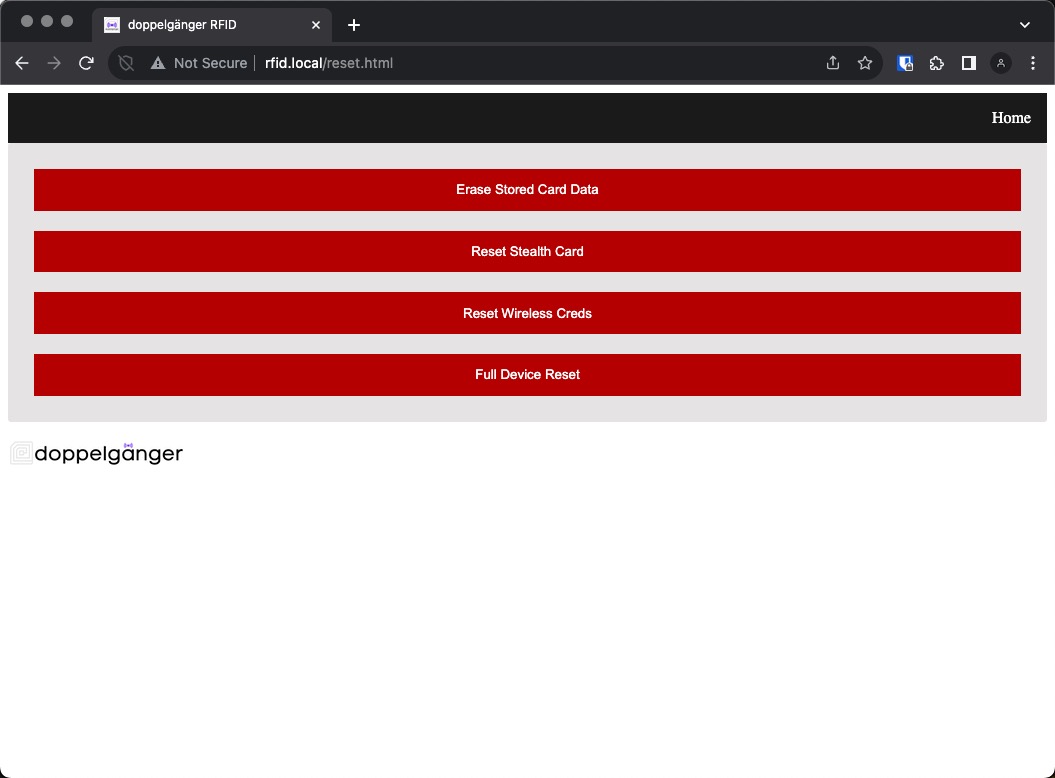
Resetting the Device & Clearing Stored Card Data
To reset the device back to it’s factory settings or to clear stored card data, navigate to the Reset page and select your desired option(s). If for whatever reason, you lock yourself out of your stealth reader (e.g., forget your wireless passphrase) - contact the PPE store with the e-mail that you used to purchase your reader.
Understanding the CSV File
Power Cycle / Bad Data
For the most part the CSV file is pretty straight forward. It provides the parsed, HEX, and binary data captured for each card. By default, Doppelgänger prevents potentially bad data captures and unparsable formats from rendering in the web application. The following screenshot illustrates “bad data.” In this case, the data captured is flicker from cycling the power. However, you will receive a simliar output if there’s EMI or if a badge crosses the reader too fast.
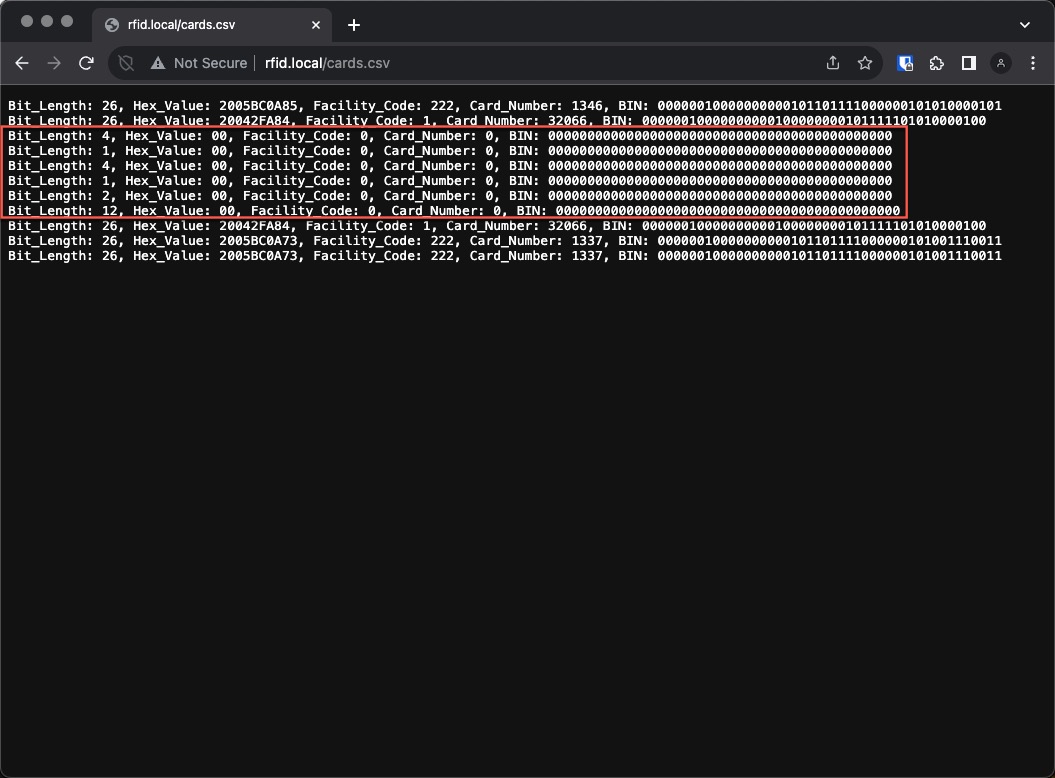
Unparsable Format
The following screenshot highlights the capture of an EM4102 card. Here you see a 32-bit capture along with data in the HEX and Binary data fields.
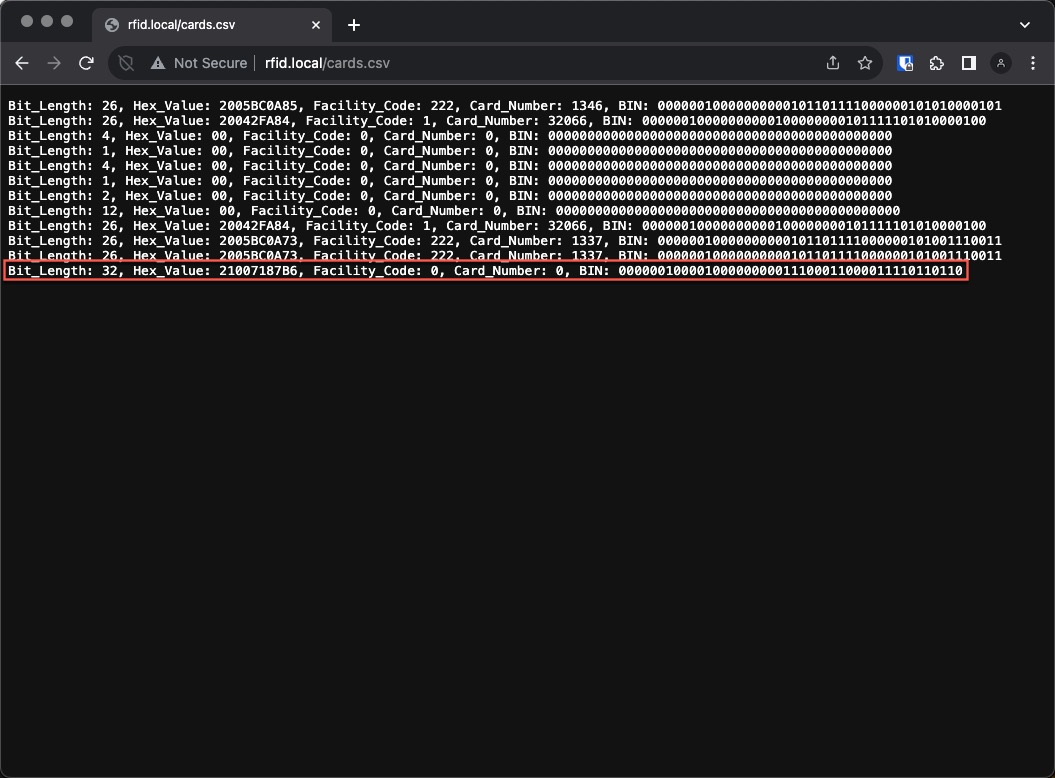
To view the Facility Code and Card Number of the captured data using the Iceman Fork of the proxmark3 firmware, copy the HEX value out and use the wiegand decode function.
# Wiegand Decode Raw (32-Bit Example)
[usb] pm3 --> wiegand decode --raw 21007187B6
[+] [HCP32 ] HID Check Point 32-bit FC: 0 CN: 58127
[+] [HPP32 ] HID Hewlett-Packard 32-bit FC: 14 CN: 102684672
[+] [Kantech ] Indala/Kantech KFS 32-bit FC: 56 CN: 50139
[+] [WIE32 ] Wiegand 32-bit FC: 113 CN: 34742
[=] found 4 matching formats
To write the captured data using the Iceman Fork of the proxmark3 firmware, copy the HEX value out and use the lf em clone function.
[usb] pm3 --> lf em 410x clone --id 21007187B6
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 21007187B6 (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff946003c717dd8e
[+] Done
[?] Hint: try `lf em 410x reader` to verify