Doppelgänger Assistant
Professional GUI application for card data calculation and Proxmark3 automation
Introduction
Doppelgänger Assistant is a professional GUI application for calculating card data and automating Proxmark3 operations for every card type that Doppelgänger Core and Stealth support. This tool streamlines the card-writing process for physical penetration testing by providing an intuitive interface with dual output displays, visual separators, and one-click clipboard copying, eliminating the need to memorize complex Proxmark3 syntax or dig through notes.
You can access the official Doppelgänger Assistant application on GitHub.
Features
- Modern GUI Interface: Intuitive two-column layout with dedicated status and command output displays
- Card Operations: Automatically generates and executes Proxmark3 commands for writing, verifying, and simulating cards
- Direct Execution: Execute write, verify, and simulate operations directly from the GUI with your Proxmark3
- Cross-Platform: Available for macOS, Linux, and Windows (via WSL)
- Card Discovery: Automatically detect card types and read card data
- Hotel Access Control: Complete MIFARE card recovery and analysis tools
- Terminal Integration: Launch Proxmark3 in a separate terminal window
Quick Install (Recommended)
The automated installers will install Doppelgänger Assistant, required dependencies, and the latest Iceman fork of Proxmark3. During installation, you’ll be prompted to select your Proxmark3 device type for optimal configuration. For detailed installation instructions and source code, visit the Doppelgänger Assistant GitHub repository.
macOS
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/tweathers-sec/doppelganger_assistant/main/installers/doppelganger_install_macos.sh)"
Linux
curl -sSL https://raw.githubusercontent.com/tweathers-sec/doppelganger_assistant/main/installers/doppelganger_install_linux.sh | sudo bash
Windows (WSL)
Open PowerShell as Administrator and run:
irm https://raw.githubusercontent.com/tweathers-sec/doppelganger_assistant/main/installers/doppelganger_install_windows.ps1 | iex
Note: The installer will prompt you to select between Ubuntu 24.04 LTS (Noble) (recommended) or Kali Linux. It will automatically detect existing installations and prompt you to update. If a reboot is required to enable WSL features, you’ll be prompted. Simply run the same command again after rebooting.
IMPORTANT: WSL2 does not support running inside nested virtual machines. The installer automatically detects and prevents installation in such environments. To proceed, install on physical hardware.
What Doppelgänger Assistant Can Do
The Doppelgänger Assistant provides a complete card analysis and cloning workflow, from initial detection through successful write operations. The application automatically identifies card technologies, extracts credential data, recovers encryption keys, and writes cloned cards with verification.
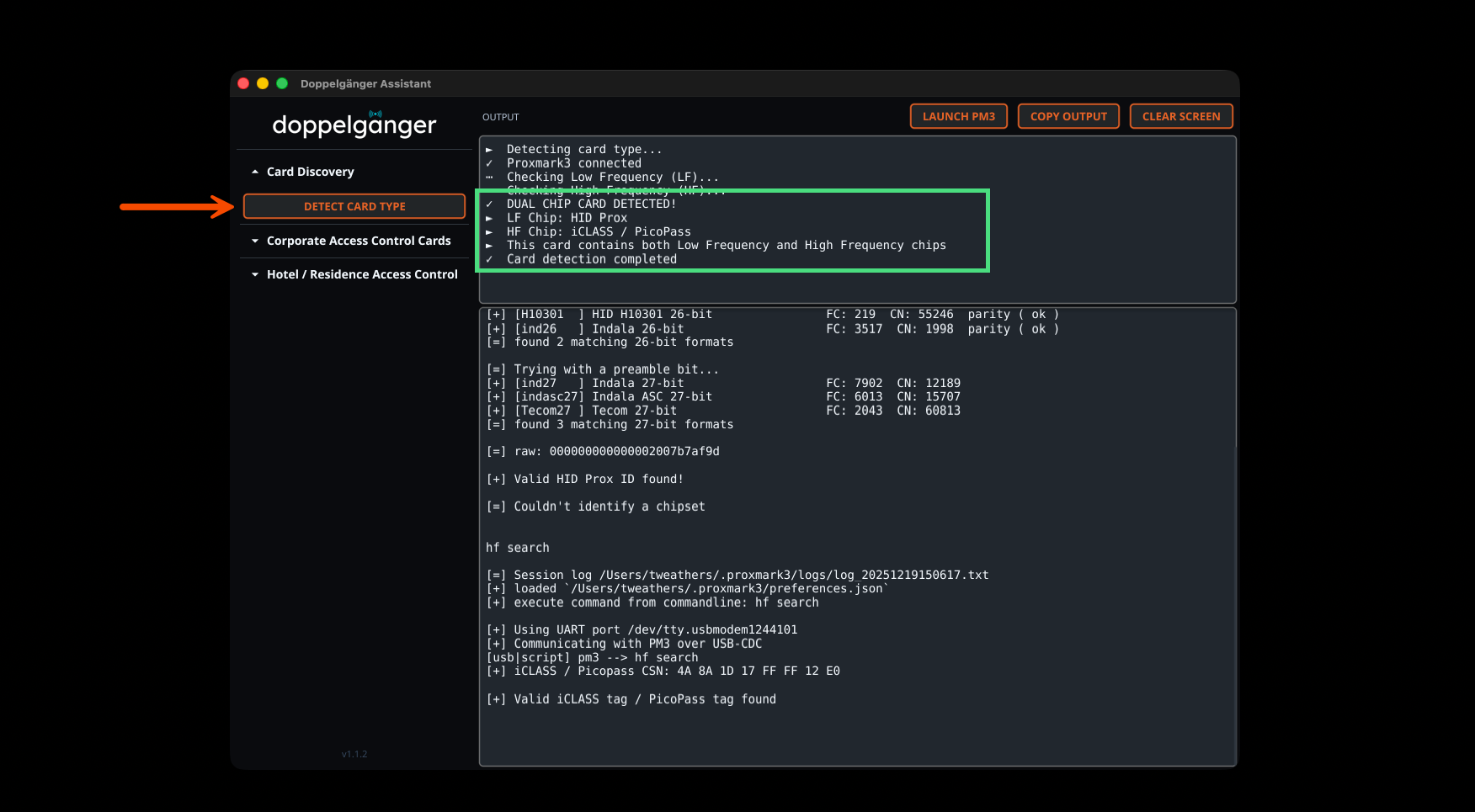
Intelligent Card Detection
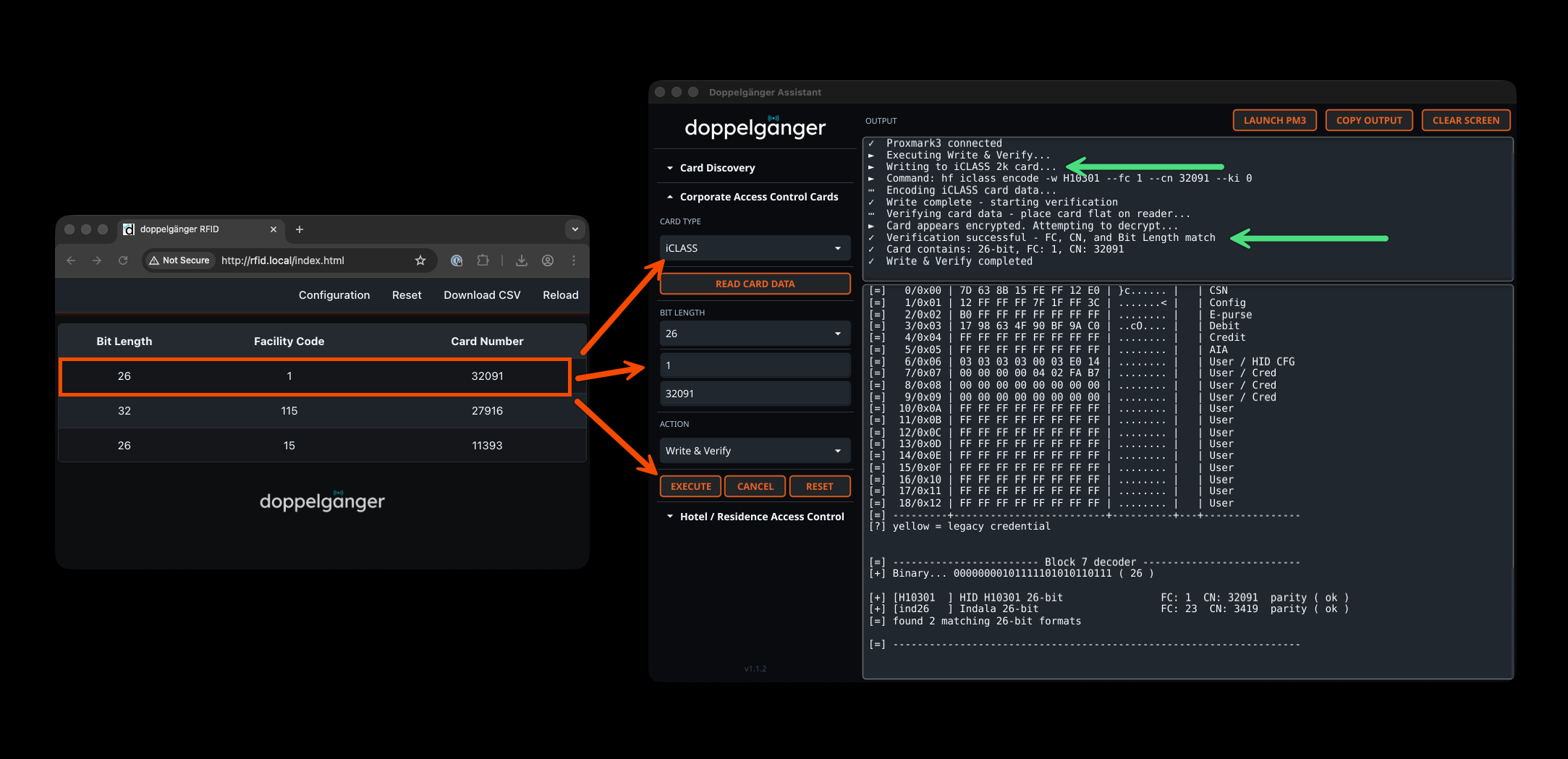
The Card Discovery feature automatically scans for both Low Frequency and High Frequency chips, identifying dual-chip cards and determining specific card technologies including HID Prox, iCLASS, PicoPass, MIFARE, and more. Results include decoded Wiegand data with facility codes and card numbers when available.
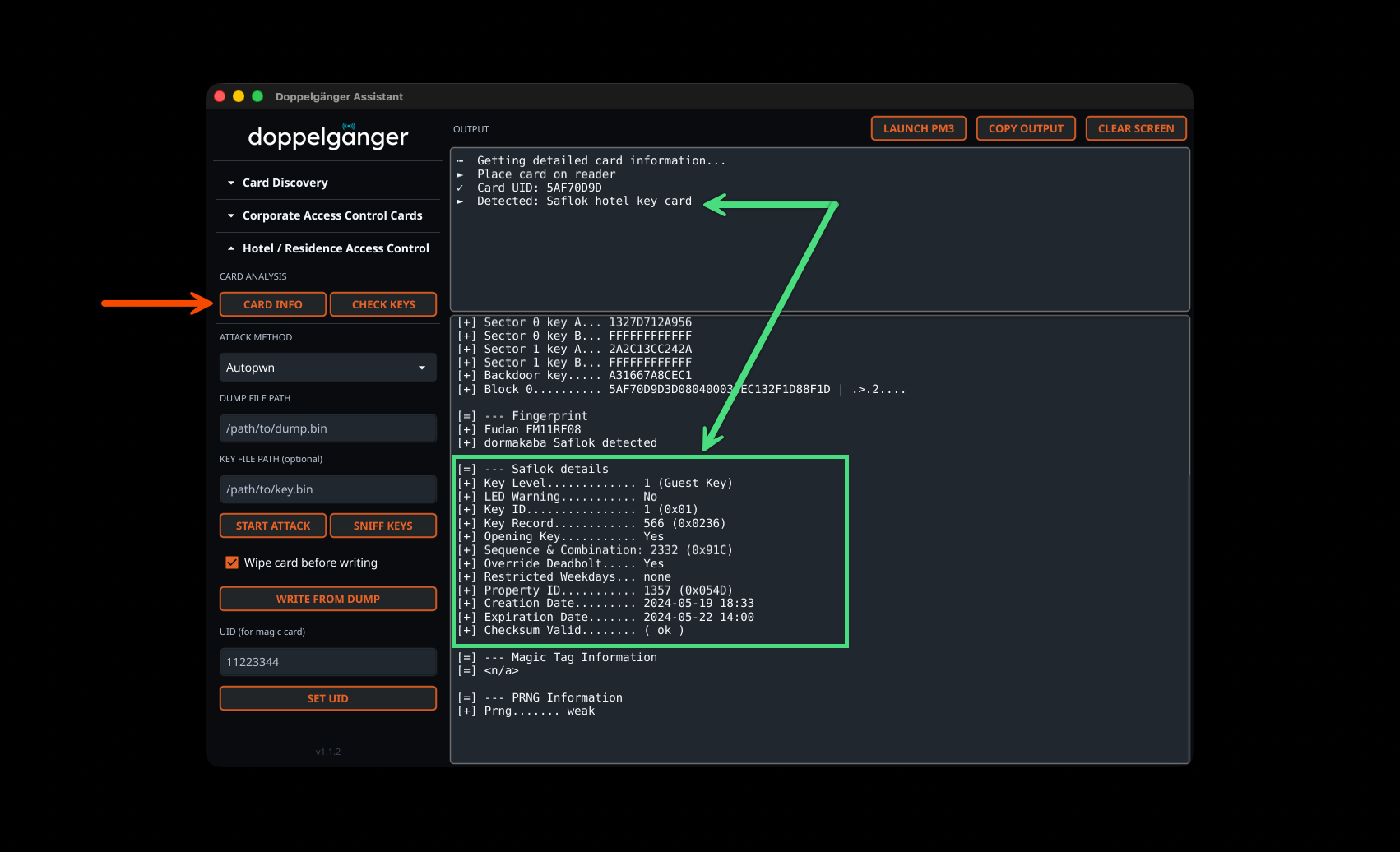
Hotel Key Card Analysis
The Hotel Access Control section provides specialized tools for MIFARE-based hotel key systems. Card Info retrieval automatically identifies Saflok hotel key cards and displays detailed card information including UID, card type, magic capabilities, and PRNG detection. The raw Proxmark3 output includes comprehensive Saflok metadata when available.
Automated Key Recovery
The MIFARE attack tools include multiple recovery methods: Autopwn (automatic multi-method), Darkside, Nested, Hardnested, Static Nested, Bruteforce, and NACK vulnerability testing. Autopwn automatically selects the best attack method based on card characteristics. Results display comprehensive recovery summaries showing sectors recovered, total keys found, recovery methods used, and automatic dump file generation for immediate card cloning.
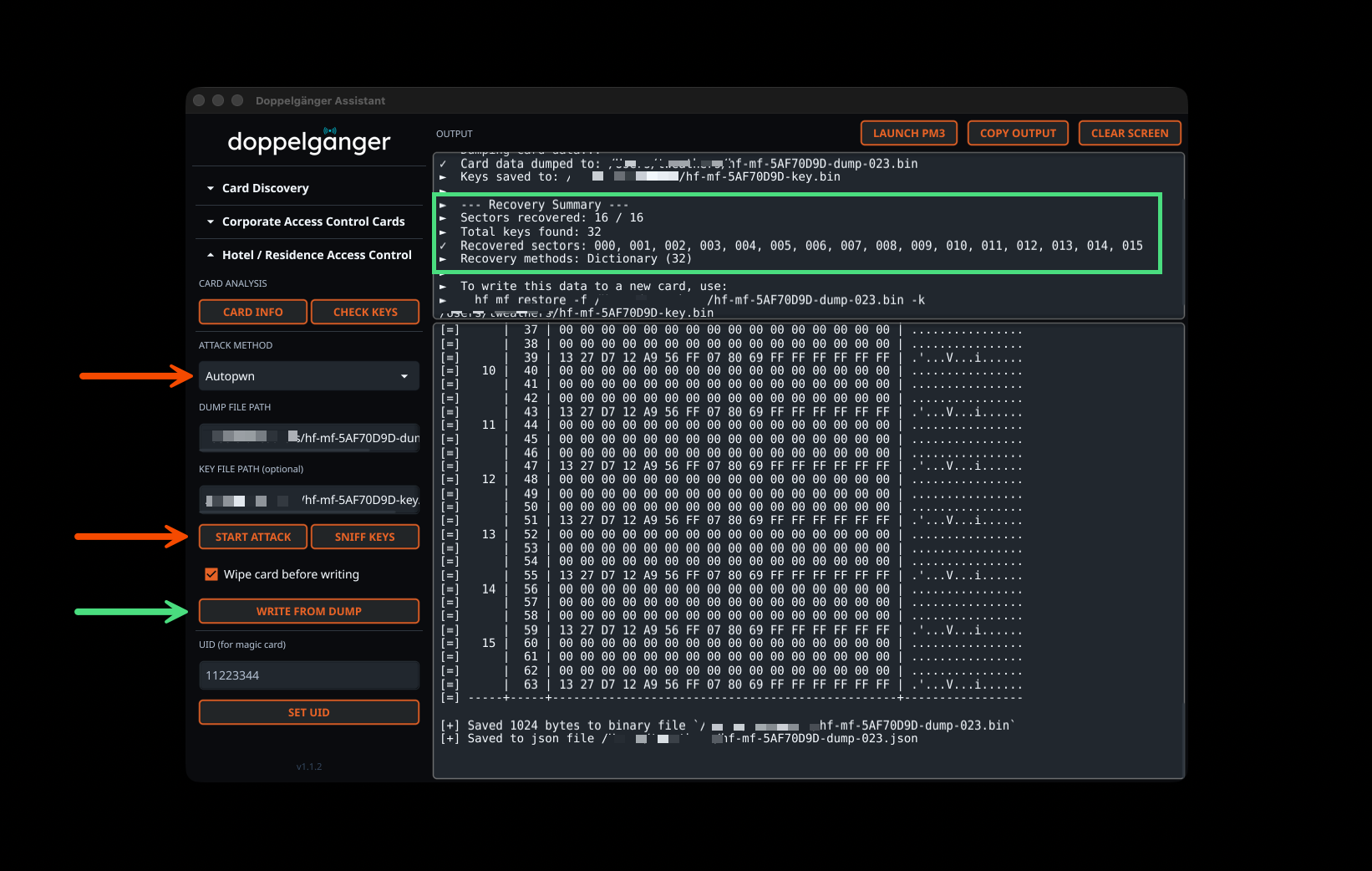
Corporate Access Card Operations
The Corporate Access Control section supports reading and writing iCLASS, PicoPass, AWID, HID Prox, Indala, Avigilon, and other corporate card technologies. Card data is automatically parsed from Proxmark3 output to extract facility codes, card numbers, bit lengths, format types (H10301, C1k35s, etc.), CSN values, and raw hex data. The integrated workflow allows immediate writing to blank cards with optional verification.
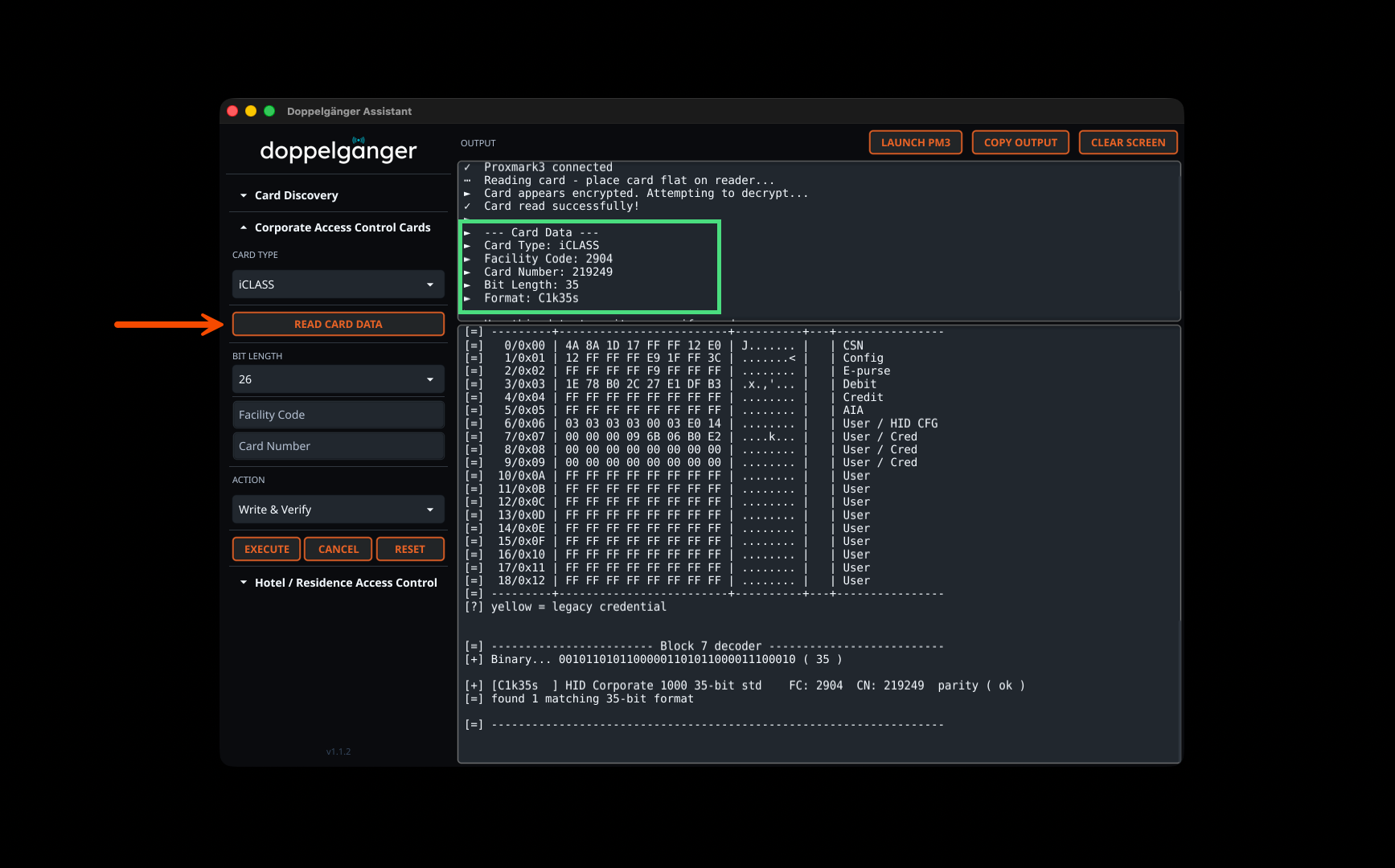
Complete Cloning Workflow
Doppelgänger Assistant integrates seamlessly with Doppelgänger RFID hardware and Proxmark3 devices. Credentials captured with Doppelgänger readers can be directly imported into the GUI for analysis and writing. The application supports reading cards from multiple manufacturers, parsing the data from the web interface, and executing write operations with real-time status updates and verification.

GUI Workflow
The Doppelgänger Assistant GUI launches by default when you run the application:
doppelganger_assistant
GUI Workflow Steps
- Select Card Type: Choose from PROX, iCLASS, AWID, Indala, Avigilon, EM4100, PIV, or MIFARE
- Choose Bit Length: Select the appropriate bit length for your card type (automatically filtered based on card type)
- Enter Card Data: Input facility code, card number, hex data, or UID as required for the selected card type
- Choose Action:
- Generate Only: Displays Proxmark3 commands for manual execution without writing
- Write & Verify: Writes card data to a blank card and verifies the result
- Simulate Card: Simulates the card using your Proxmark3 device
- Execute: Click the EXECUTE button to run the operation
- Monitor Output:
- Status Output (top panel): Color-coded status messages with operation progress
- Command Output (bottom panel): Detailed Proxmark3 command results with visual separators
- Copy Results: Click COPY OUTPUT to copy all command results to your clipboard
- Reset: Click RESET to clear all fields and start over
The dual output panels provide clear separation between status updates and command results, with visual spacers (e.g., |----------- WRITE #1 -----------|) making it easy to distinguish between multiple write attempts or verification steps.
Video Demo
The following video illustrates the writing of a captured Seos card to an iClass 2k card using a PPE MFAS Reader and Doppelgänger Assistant.
Doppelgänger Devices
You can purchase a Stealth reader, Doppelgänger Dev Board, or fully assembled long-range readers from the Physical Exploitation Store. For the open-source firmware, check out Doppelgänger Core.
Supported Proxmark3 Devices
Doppelgänger Assistant works with the Iceman fork of Proxmark3 and supports the following device types:
- Proxmark3 RDV4 - With or without Blueshark Bluetooth addon
- Proxmark3 Easy (512KB) - Generic platform support
The automated installers will prompt you to select your device type during installation for optimal configuration.
Corporate PACS Card Types
Below are the officially supported corporate PACS card types based on Doppelgänger firmware. Hotel/MIFARE key card support was added in version 1.1.2 with key recovery and cloning capabilities.
Note: Hotel key card / detailed MIFARE analysis is not in alignment with captured data using Doppelgänger products. This is just an added feature to support physical penetration testing efforts and is considered a work in progress.
| Card Types | Core | Stealth | FC Range | CN Range |
|---|---|---|---|---|
| Keypad PIN Codes | X | N/A | N/A | |
| HID H10301 26-bit | X | X | 0–255 | 0–65,535 |
| Indala 26-bit | X | X | 0–255 | 0–65,535 |
| Indala 27-bit | X | X | 0–4,095 | 0–8,191 |
| 2804 WIEGAND 28-bit | X | X | 0–255 | 0–16,383 |
| Indala 29-bit | X | X | 0–4,095 | 0–32,767 |
| ATS Wiegand 30-bit | X | X | 0–2,047 | 0–32,767 |
| HID ADT 31-Bit | X | X | 0–15 | 0–8,388,607 |
| EM4102 / Wiegand 32-bit | X | X | 0–32,767 | 0–65,535 |
| HID D10202 33-bit | X | X | 0–127 | 0–16,777,215 |
| HID H10306 34-bit | X | X | 0–65,535 | 0–65,535 |
| HID Corporate 1000 35-bit | X | X | 0–4,095 | 0–1,048,575 |
| HID Simplex 36-bit (S12906) | X | X | 0–255 | 0–65,535 |
| HID H10304 37-bit | X | X | 0–65,535 | 0–524,287 |
| HID H800002 46-bit | X | X | 0–16,383 | 0–1,073,741,823 |
| HID Corporate 1000 48-bit | X | X | 0–4,194,303 | 0–8,388,607 |
| Avigilon 50-bit | X | X | 0–65,535 | 0–8,388,607 |
| Avigilon 56-bit | X | X | 0–1,048,575 | 0–4,194,303 |
| C910 PIVKey | X | X | N/A | N/A |
| MIFARE (Various Types) | X | X | N/A | N/A |
Supported technologies include:
- iCLASS (Legacy/SE/Seos)
- PROX
- Indala
- AWID
- Avigilon
- EM4102
- PIV (UID Only - As that is what is provided via the readers wiegand output)
- MIFARE (UID Only - As that is what is provided via the readers wiegand output)
iCLASS SE/Seos Cards: Captured SE and Seos cards can only be written to iCLASS 2k cards.
Detailed Installation Instructions
Manual macOS Installation
-
Download the appropriate DMG file for your architecture from the release page:
- Apple Silicon (M1/M2/M3):
doppelganger_assistant_darwin_arm64.dmg - Intel:
doppelganger_assistant_darwin_amd64.dmg
- Apple Silicon (M1/M2/M3):
-
Open the DMG file and drag
doppelganger_assistant.appto your/Applicationsfolder -
Remove quarantine attributes:
xattr -cr /Applications/doppelganger_assistant.app -
Create a command-line alias by adding to your shell profile (
~/.zshrcor~/.zprofile):alias doppelganger_assistant='/Applications/doppelganger_assistant.app/Contents/MacOS/doppelganger_assistant' -
Reload your shell:
source ~/.zshrc
Manual Linux Installation
Option 1: Using .deb package (Debian/Ubuntu/Kali - Recommended)
-
Install dependencies:
sudo apt update && sudo apt upgrade -y sudo apt install libgl1 xterm wget -y -
Download and install the .deb package for your architecture:
# For x86_64/amd64 systems: wget https://github.com/tweathers-sec/doppelganger_assistant/releases/latest/download/doppelganger_assistant_linux_amd64.deb sudo dpkg -i doppelganger_assistant_linux_amd64.deb # For ARM64 systems: wget https://github.com/tweathers-sec/doppelganger_assistant/releases/latest/download/doppelganger_assistant_linux_arm64.deb sudo dpkg -i doppelganger_assistant_linux_arm64.deb -
Fix any missing dependencies (if needed):
sudo apt-get install -f -y
Option 2: Using tar.xz archive (Other distributions)
-
Install dependencies:
sudo apt update && sudo apt upgrade -y sudo apt install libgl1 xterm make git wget -y -
Download and install for your architecture:
# For x86_64/amd64 systems: wget https://github.com/tweathers-sec/doppelganger_assistant/releases/latest/download/doppelganger_assistant_linux_amd64.tar.xz # For ARM64 systems: wget https://github.com/tweathers-sec/doppelganger_assistant/releases/latest/download/doppelganger_assistant_linux_arm64.tar.xz # Extract and install: tar xvf doppelganger_assistant_linux_*.tar.xz cd doppelganger_assistant sudo make install cd .. rm -rf doppelganger_assistant
To launch the Doppelgänger Assistant GUI:
doppelganger_assistant
Manual Windows (WSL) Installation
-
Enable WSL and install a Linux distribution. Open PowerShell as Administrator:
# For Ubuntu 24.04 LTS (recommended): wsl --install -d Ubuntu-24.04 # OR for Kali Linux: wsl --install -d kali-linux -
Reboot Windows. After reboot, WSL will finish setup. When prompted, create a username and password for your Linux environment.
-
Install Doppelgänger Assistant (inside WSL):
sudo apt update && sudo apt upgrade -y sudo apt install libgl1 xterm wget -y # For x86_64/amd64 systems: wget https://github.com/tweathers-sec/doppelganger_assistant/releases/latest/download/doppelganger_assistant_linux_amd64.deb sudo dpkg -i doppelganger_assistant_linux_amd64.deb # For ARM64 systems: wget https://github.com/tweathers-sec/doppelganger_assistant/releases/latest/download/doppelganger_assistant_linux_arm64.deb sudo dpkg -i doppelganger_assistant_linux_arm64.deb -
Install Proxmark3 dependencies:
sudo apt install --no-install-recommends -y git ca-certificates build-essential pkg-config \ libreadline-dev gcc-arm-none-eabi libnewlib-dev qtbase5-dev \ libbz2-dev liblz4-dev libbluetooth-dev libpython3-dev libssl-dev libgd-dev -
Clone and build Proxmark3:
mkdir -p ~/src && cd ~/src git clone https://github.com/RfidResearchGroup/proxmark3.git cd proxmark3 # Configure for your Proxmark3 device type: cp Makefile.platform.sample Makefile.platform # Edit Makefile.platform for your device: # - For RDV4 with Blueshark: Uncomment PLATFORM=PM3RDV4 and PLATFORM_EXTRAS=BTADDON # - For RDV4 without Blueshark: Uncomment PLATFORM=PM3RDV4 only # - For Proxmark3 Easy (512KB): Uncomment PLATFORM=PM3GENERIC and PLATFORM_SIZE=512 nano Makefile.platform # Build and install make clean && make -j$(nproc) sudo make install PREFIX=/usr/local -
Install USBipd (from Windows PowerShell as Administrator):
winget install --interactive --exact dorssel.usbipd-win -
Connect Proxmark3 to WSL (from Windows cmd.exe or PowerShell as Administrator):
usbipd list # List USB devices - find your Proxmark3 (VID: 9ac4) usbipd bind --busid 9-1 # Replace 9-1 with your Proxmark3's busid usbipd attach --wsl --busid 9-1 # Attach to WSL
To launch Doppelgänger Assistant:
doppelganger_assistant
Updating
Updating Windows (WSL) Installation
Automated Update (Recommended)
Run the update script from the installation directory:
powershell -ExecutionPolicy Bypass -File C:\doppelganger_assistant\wsl_update.ps1
Or download and run directly from GitHub:
powershell -ExecutionPolicy Bypass -Command "irm https://raw.githubusercontent.com/tweathers-sec/doppelganger_assistant/main/scripts/wsl_update.ps1 | iex"
The update script will:
- Download the latest Doppelgänger Assistant binary
- Update all scripts and installers from the repository
- Update and rebuild Proxmark3 from source
- Preserve your WSL configuration and settings
Updating macOS or Linux Installation
Re-run the installer script. It will detect the existing installation and prompt you to update:
macOS:
bash <(curl -fsSL https://raw.githubusercontent.com/tweathers-sec/doppelganger_assistant/main/installers/doppelganger_install_macos.sh)
Linux:
bash <(curl -fsSL https://raw.githubusercontent.com/tweathers-sec/doppelganger_assistant/main/installers/doppelganger_install_linux.sh)
Uninstallation
Uninstalling from Windows (WSL)
Automated Uninstall (Recommended)
Download and run the uninstaller directly from GitHub:
powershell -ExecutionPolicy Bypass -Command "irm https://raw.githubusercontent.com/tweathers-sec/doppelganger_assistant/main/scripts/uninstall.ps1 | iex"
Manual Uninstall
If you have Doppelgänger Assistant installed, run the uninstall script:
powershell -ExecutionPolicy Bypass -File C:\doppelganger_assistant\uninstall.ps1
The uninstaller will:
- Stop and unregister WSL distributions (Kali-doppelganger_assistant or Ubuntu-doppelganger_assistant)
- Remove all files from
C:\doppelganger_assistant - Delete the desktop shortcut
- Uninstall usbipd (it will be reinstalled if you run the installer again)
Note: The script automatically relocates itself to a temporary directory to ensure clean removal of the installation directory.
Uninstalling from macOS
To uninstall from macOS:
sudo rm -rf /Applications/doppelganger_assistant.app
sudo rm /usr/local/bin/doppelganger_assistant
Uninstalling from Linux
If installed via .deb package:
sudo apt remove doppelganger-assistant
If installed via tar.xz archive:
sudo rm /usr/local/bin/doppelganger_assistant
rm -f ~/.local/share/applications/doppelganger_assistant.desktop
rm -f ~/Desktop/doppelganger_assistant.desktop
sudo rm /usr/share/pixmaps/doppelganger_assistant.png
Development
Building from Source
To build Doppelgänger Assistant from source:
# Clone the repository
git clone https://github.com/tweathers-sec/doppelganger_assistant.git
cd doppelganger_assistant
# Build for current platform
./build.sh
# Build for all platforms (requires Docker)
./build_all.sh
Project Structure
src/- Contains all Go source code and module filesinstallers/- Platform-specific installation scriptsscripts/- Utility scripts for WSL and Windows setupbuild.sh- Single-platform build scriptbuild_all.sh- Multi-platform build script using fyne-cross
Contributing
- Fork the repository
- Create a feature branch
- Make your changes in the
src/directory - Test your changes with
./build.sh - Submit a pull request
Changelog
Version 1.1.2 (December 18, 2025)
New Features:
- Added LAUNCH PM3 button to open Proxmark3 in a separate terminal window
- Added Card Discovery section with automatic card type detection
- Added READ CARD DATA functionality for all supported card types
- Added Hotel / Residence Access Control section with MIFARE tools
- Added dual chip card detection for cards with both LF and HF capabilities
- Added automatic card info retrieval when MIFARE cards are detected
Improvements:
- Improved card detection to show specific MIFARE types and magic capabilities
- Enhanced card verification with clearer success messages
- Better error handling and user feedback throughout the application
- Improved iCLASS card reading with automatic decryption support
Version 1.1.1
- Initial release with core card writing, verification, and simulation features
- Support for PROX, iCLASS, AWID, Indala, Avigilon, EM4100, PIV, and MIFARE cards
License Information
This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
You are free to:
- Share – Copy and redistribute the material in any medium or format
Under these terms:
- Attribution – Provide appropriate credit, a link to the license, and indicate if changes were made
- NonCommercial – Do not use the material for commercial purposes
- NoDerivatives – Do not distribute modified versions
Full license details are available in the LICENSE file.
Legal Notice
This application is intended strictly for authorized penetration testing and security assessments. Unauthorized or illegal use is the sole responsibility of the user. Mayweather Group LLC, Practical Physical Exploitation, and its creators assume no liability for misuse or unauthorized application of this tool.
Support
For professional support and documentation, visit:
Credits
Developed by Travis Weathers (@tweathers-sec)
Copyright © 2025 Mayweather Group, LLC
This software works in conjunction with Doppelgänger Core and Doppelgänger hardware devices.