Doppelgänger Core
For Physical Security Practitioners, by a Physical Security Practitioner

Introduction
Doppelgänger Core is a professional-grade RFID cloning and analysis tool designed specifically for penetration testing applications. It merges the best features of the Doppelgänger Community and Pro firmware into a unified platform, optimized exclusively for the Doppelgänger RFID Development Board. Core simplifies capturing and analyzing RFID access control card data while maintaining operational security and ease of use.
To purchase the Doppelgänger RFID Development Board, visit the Practical Physical Exploitation Store. Detailed specifications and documentation are available here.
You can access the official Doppelgänger Core firmware on GitHub.
Firmware Updates
Current Version: 1.1.0
Build Date: 2025-10-02
Highlights
- Added HID H800002 46-bit support
- Facility Code: 14 bits (bits 1–14)
- Card Number: 30 bits (bits 15–44)
- Added Avigilon Avig56 56-bit support
- Default extraction mapping in firmware: FC = bits 1–32 shifted right by 12; CN = bits 33–54
- Note: Avigilon ACM allows site-configurable FC/CN lengths within the 54-bit payload
Download Latest Firmware
Visit the Doppelgänger Core GitHub Releases page to download the latest firmware version.
COMPATIBILITY WARNING: This firmware is ONLY compatible with Doppelgänger Core and Doppelgänger RFID Development Board devices.
DO NOT flash this firmware on:
- Doppelgänger Breakout Board (End-of-life)
- Doppelgänger Pro (End-of-life)
- Doppelgänger Community (End-of-life)
- Stealth v1 or v2 devices
Flashing incompatible firmware will cause operational issues. Flash at your own risk!
Supported Card Formats
Wiegand Formats
Below are the card data formats supported by Doppelgänger Core. Bit positions listed exclude parity bits, and actual implementation may vary by reader.
| Card Type | Format | Facility Code Bits | Card Number Bits | Notes |
|---|---|---|---|---|
| HID H10301 | 26-bit | 8 (1–8) | 16 (9–24) | Standard Prox |
| Indala | 26-bit | 8 (1–8) | 16 (9–25) | Requires Indala reader |
| Indala | 27-bit | 12 (1–12) | 13 (14–26) | Requires Indala reader |
| 2804 WIEGAND | 28-bit | 8 (4–11) | 14 (13–26) | Custom format |
| Indala | 29-bit | 12 (1–12) | 15 (14–28) | Requires Indala reader |
| ATS Wiegand | 30-bit | 11 (2–12) | 15 (14–28) | Custom format |
| HID ADT | 31-bit | 4 (1–4) | 23 (5–27) | ADT specific format |
| WEI32 (EM4102) | 32-bit | 15 (1–15) | 16 (16–31) | EM4102 format |
| HID D10202 | 33-bit | 7 (1–7) | 24 (8–31) | Extended format |
| HID H10306 | 34-bit | 16 (1–16) | 16 (17–32) | Extended format |
| HID Corporate 1000 | 35-bit | 12 (2–13) | 20 (14–33) | Corporate format |
| HID Simplex (S12906) | 36-bit | 8 (1–8) | 16 (19–34) | Simplex format |
| HID H10304 | 37-bit | 16 (1–16) | 19 (17–35) | Extended format |
| HID H800002 | 46-bit | 14 (1–14) | 30 (15–44) | HID H800002 format |
| HID Corporate 1000 | 48-bit | 22 (2–23) | 23 (24–46) | Extended Corp format |
| Avigilon Avig56 | 56-bit | Configurable (N) | Configurable (54−N) | 28/28 parity; site-configurable FC/CN |
iCLASS Formats
| Card Type | Notes |
|---|---|
| iCLASS Standard | Legacy iCLASS cards |
| iCLASS SE | Secure Element cards |
| iCLASS Seos | Latest-generation secure cards |
| PIV/MF Cards | UID extraction only (UID provided in data stream) |
Additional Wiegand Features
- Keypad PIN capture (4-bit)
- Raw binary data capture
- Error detection and filtering
- Parity bit validation
Firmware Features
- Wireless configuration manager
- Device egress and team access via mobile hotspot
- mDNS access: http://rfid.local/
- Optional email/text notifications
- Web interface for viewing, sorting, and downloading captured card data
- Web-based reset functionality
- Configurable GPIO support for external sensors or relays
Initial Setup Instructions
We recommend configuring Doppelgänger Core initially via a computer. After setup, the device can operate independently.
- Apply power to the device.
- If the blue LED is lit, the device is in configuration mode.
- Connect to the wireless network named doppelgänger_XXXX (default password: UndertheRadar).
- The Captive Portal should launch automatically. If not, manually navigate to http://192.168.4.1.
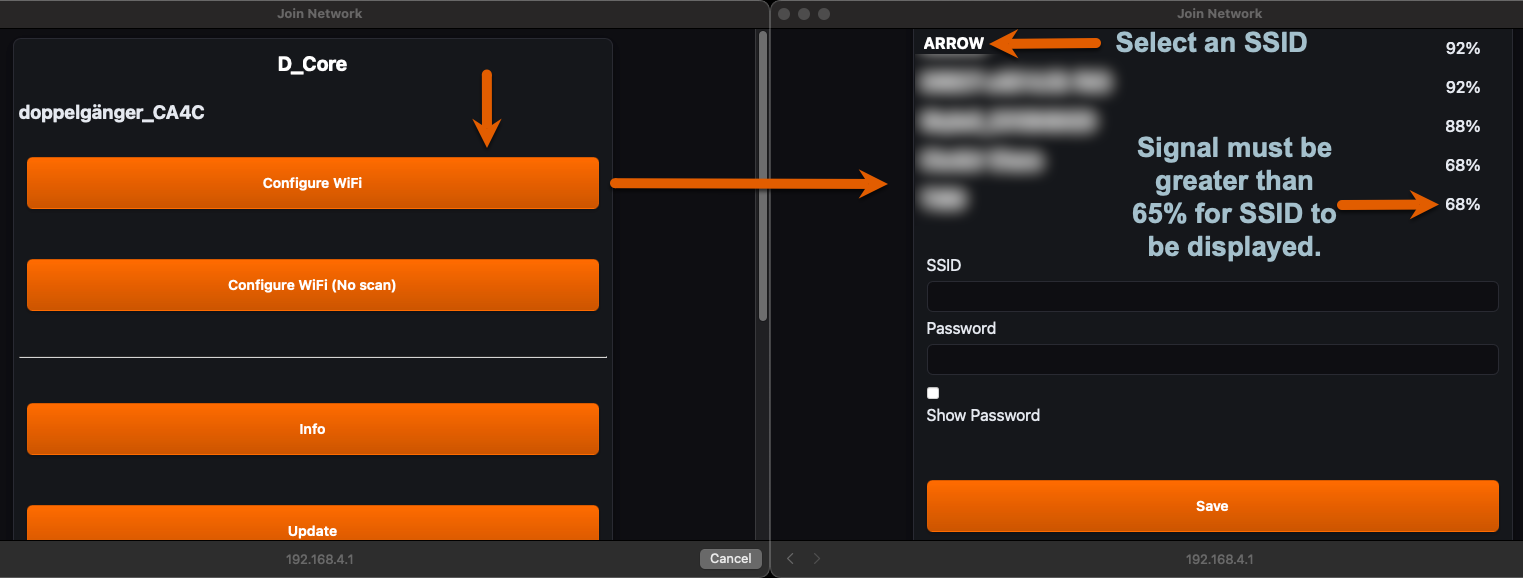
Captive Portal Menu Options
- Configure WiFi: Scan and select wireless networks (RSSI-based filtering included).
- Configure WiFi (No Scan): Manually configure without scanning.
- Info: View device stats; erase Wi-Fi credentials (email config retained).
- Update: Perform OTA firmware updates.
- Restart: Restart the device.
- Exit: Close the portal.
Mobile Device Connectivity
-
iPhone:
Enable Maximize Compatibility in Personal Hotspot settings and keep the hotspot menu open during configuration. Connect via Captive Portal. -
Android:
Procedure is similar to iPhone (testing pending).
Once configured, access the Doppelgänger web app at: http://rfid.local
Reconnection Process
Ensure your mobile hotspot is active before powering on Doppelgänger. If the device doesn’t detect the hotspot, it will enter configuration mode automatically. It retries every 120 seconds, or you can manually reboot via the Captive Portal.
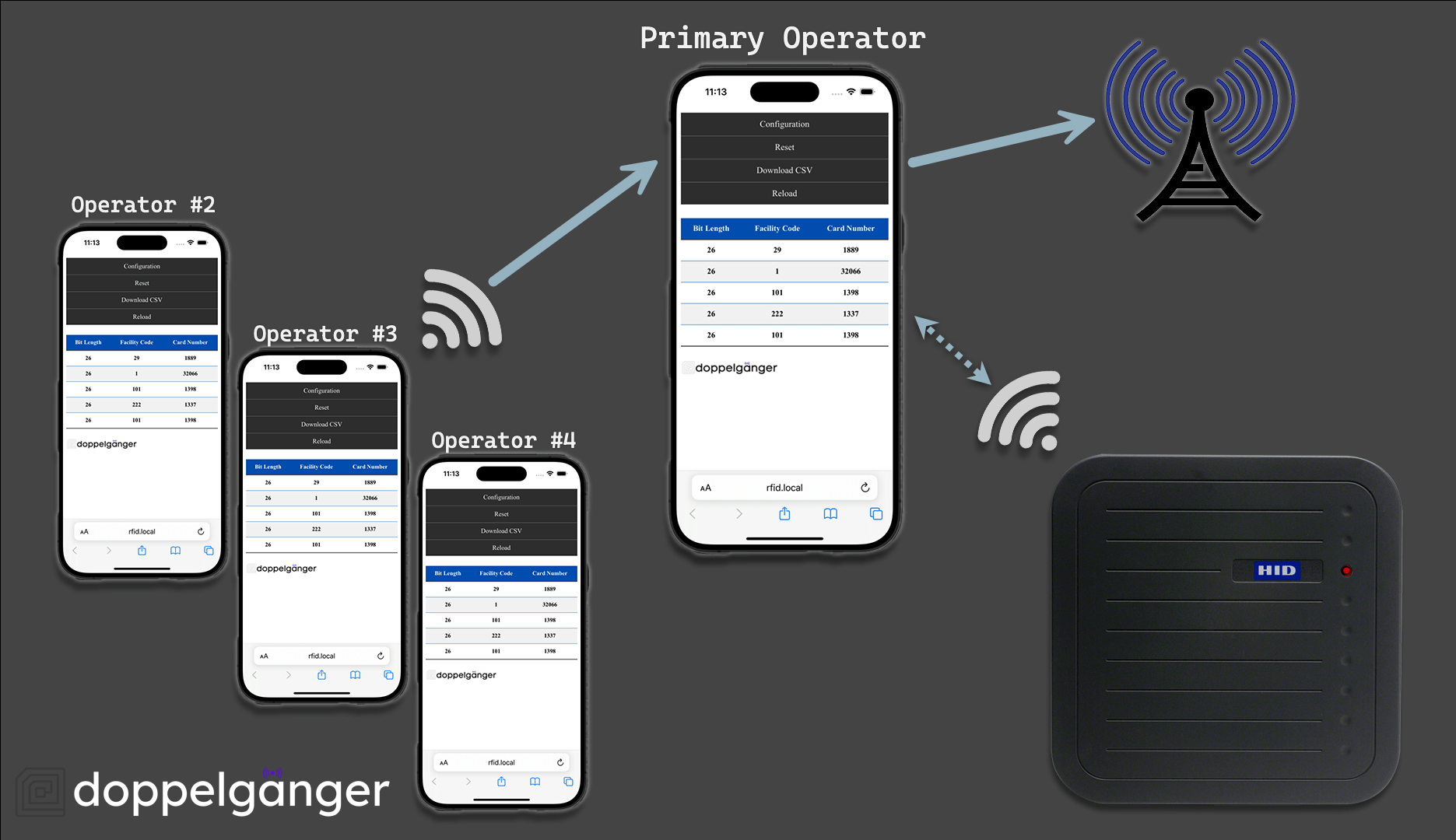
Multi-Operator Operation
Multiple operators can access the Doppelgänger Core web interface by connecting to the same wireless hotspot that the device is tethered to. The following graphic illustrates the connectivity flow:
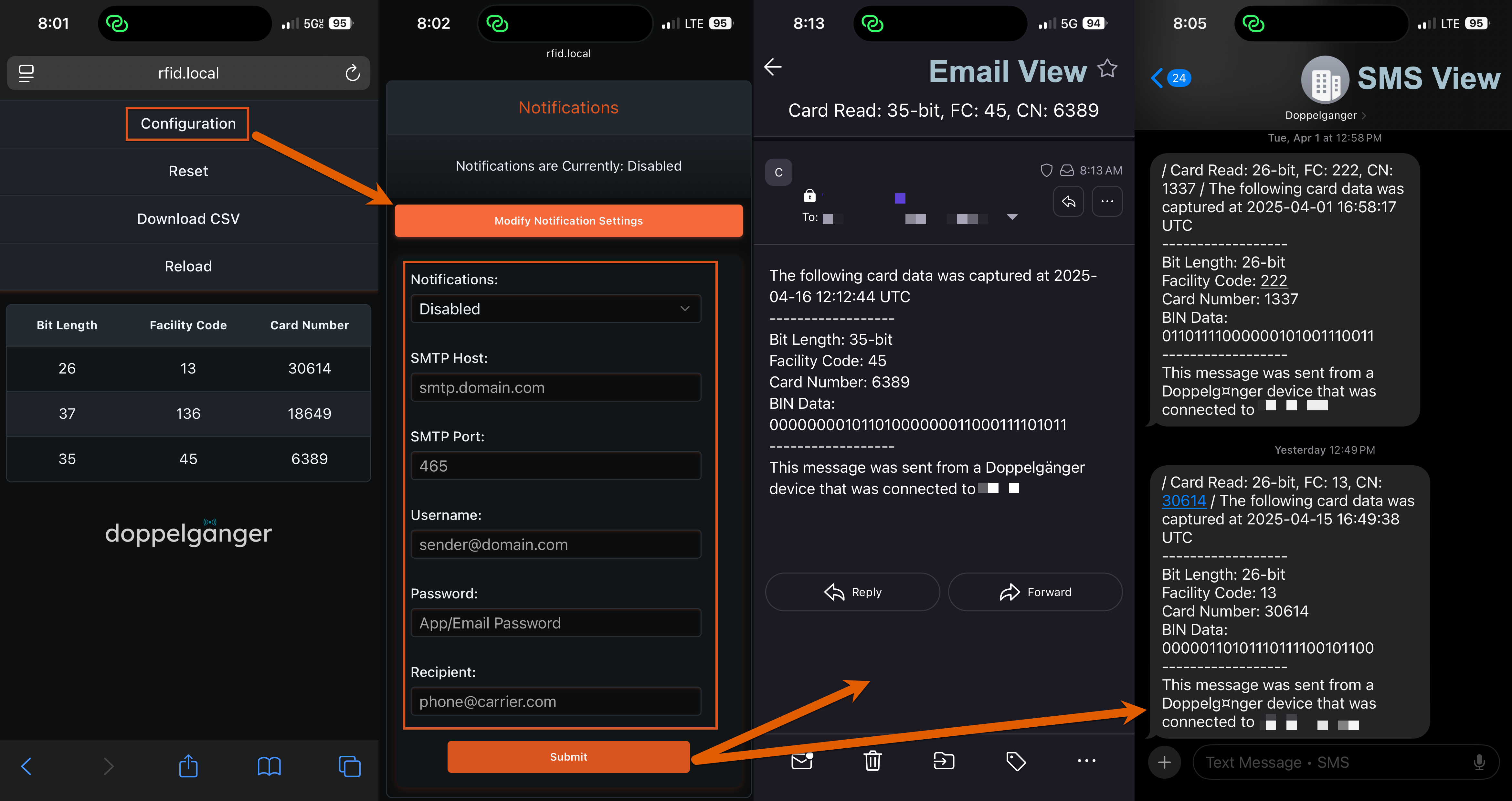
Email & Text Notifications Setup
Configure notifications through the Notifications tab in the Doppelgänger web app. SMTP credentials are stored securely.
Text notification format:
Verizon: [email protected]
AT&T: [email protected]
T-Mobile: [email protected]
Google-Fi: [email protected]
Gmail Notification Account Setup
To enable Gmail notifications, enable 2-Step Verification and create an App Password:
- Set up a new Gmail account
- Enable 2-Step Verification
- Create an App Password via your Google Account under Security → App Passwords
- Select “Mail” and “Other” named “Doppelgänger”
- Use the generated password for notification setup
Gmail SMTP Settings:
| SMTP Server | SMTP Port |
|---|---|
| smtp.gmail.com | 465 (SSL) |
Serial Debugging
Serial debugging can be enabled or disabled from the Configuration Menu. Why disable it? Operational security (OPSEC).
Note: You should enable Serial Debugging prior to upgrading firmware.
Connect the Doppelgänger RFID Dev Board via USB-C to your computer:
macOS
ls /dev/cu.usbmodem*
screen /dev/cu.usbmodemXXXXX 115200
Linux
ls /dev/ttyUSB*
screen /dev/ttyUSBX 115200
Or use PlatformIO’s serial console:
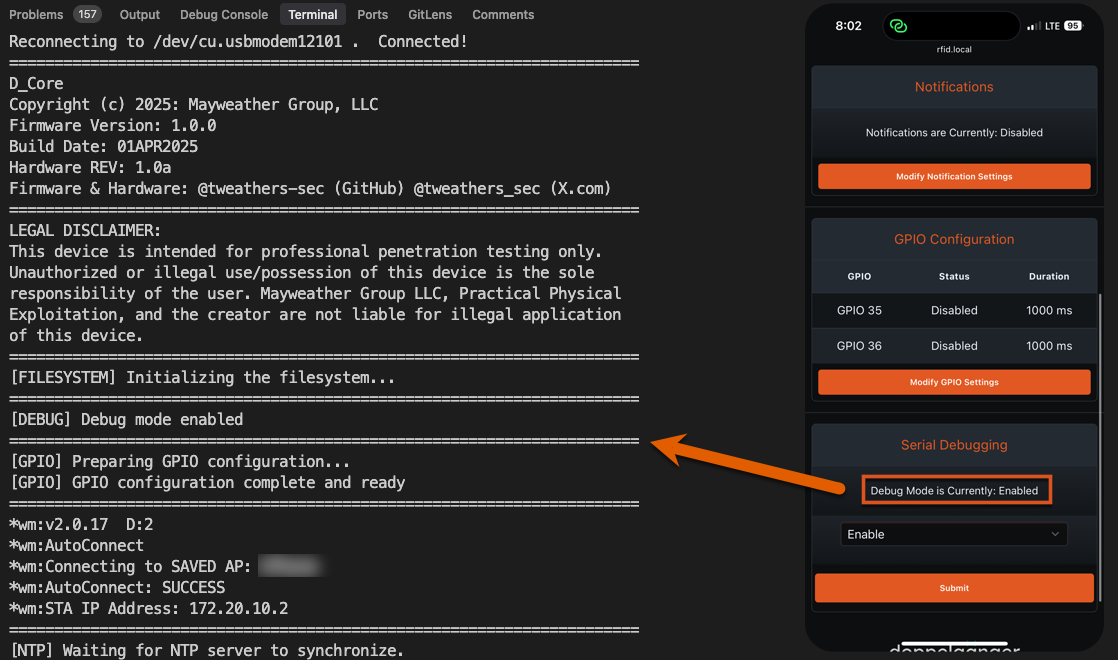
Once connected, the serial console provides detailed status messages during boot, configuration, and runtime. This information is useful for troubleshooting and verifying proper functionality.
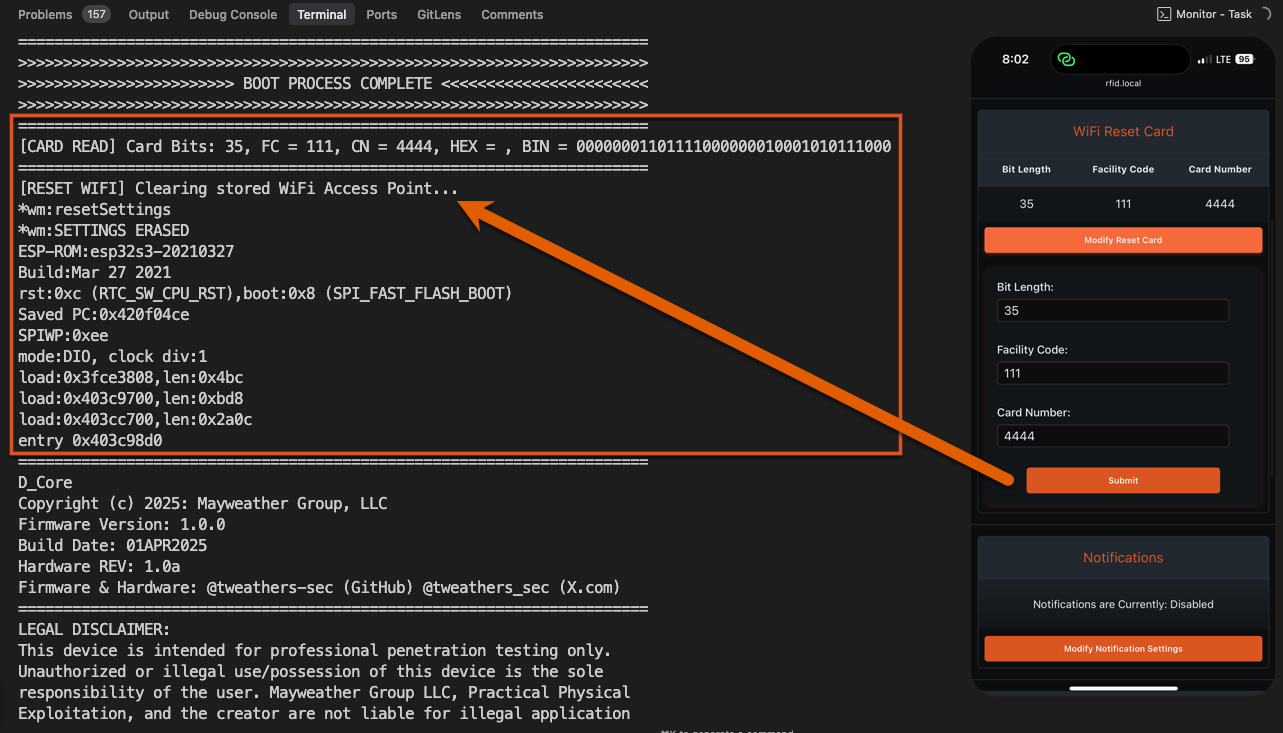
WiFi Reset Card
The WiFi Reset Card is designed to erase stored wireless credentials. This is especially useful for rotational gear shared between team members. Doppelgänger stores credentials when connecting to a hotspot so it can auto-reconnect on future boots. If someone forgets to wipe credentials, use the WiFi Reset Card.
We recommend customizing this card with unique values.
GPIO Settings
The image below illustrates a haptic (vibration) sensor installed on GPIO36. When enabled, the sensor will vibrate for 3000ms (3 seconds) upon a successful card read.

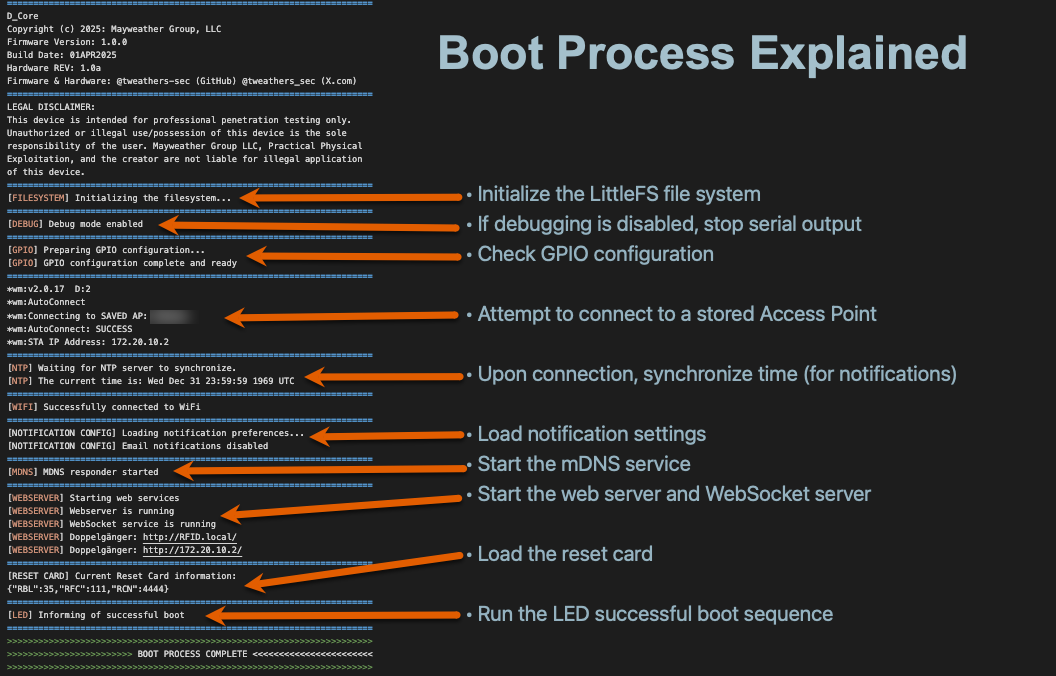
Doppelgänger Operational Processes Explained
The diagrams below illustrate Doppelgänger’s internal processes, including boot sequences, configuration mode logic, and how captured card data is handled.
Boot Process Overview
Upon power-up, Doppelgänger follows this sequence:
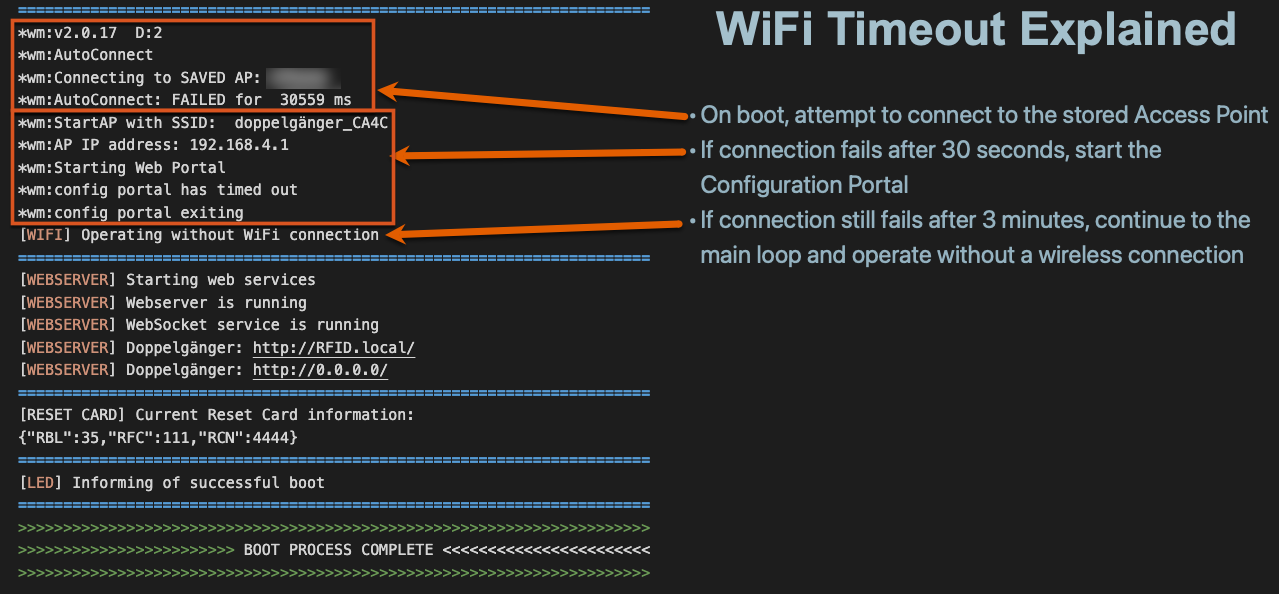
Configuration Mode Timeout Logic
If Doppelgänger fails to connect to a known wireless network within 30 seconds, it enters Configuration Mode to allow manual setup via the Captive Portal. If it fails again, it skips wireless setup entirely and proceeds into the main loop, allowing you to continue capturing card data.
Writing Captured Card Data
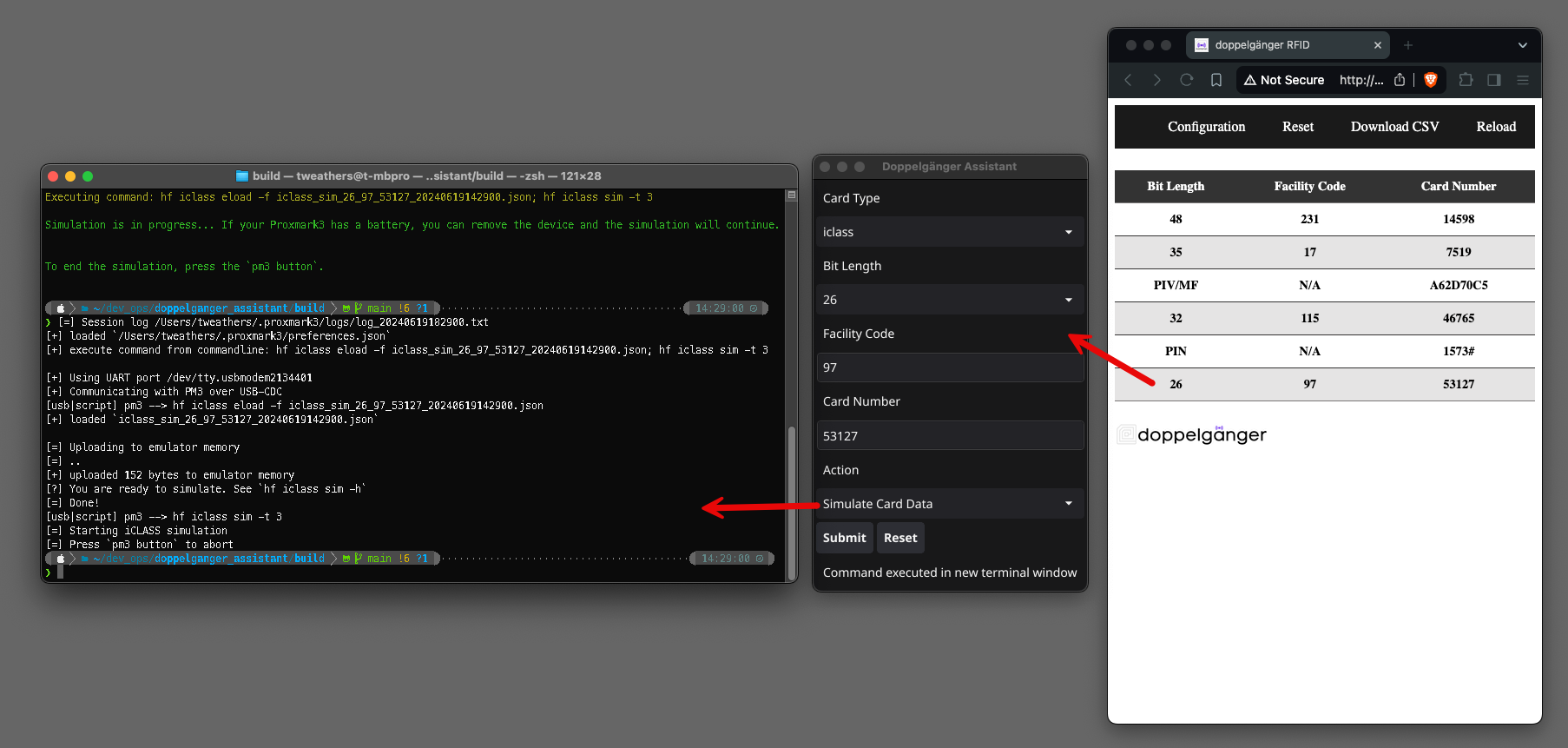
To efficiently manage and write captured RFID data, use the official Doppelgänger Assistant application. This tool simplifies generating Proxmark3 commands, writing data to blank RFID cards, and simulating captured card data. Doppelgänger Assistant supports macOS, Linux, and Windows (via WSL).
License Information
This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
You are free to:
- Share – Copy and redistribute the material in any medium or format
Under these terms:
- Attribution – Provide appropriate credit, a link to the license, and indicate if changes were made
- NonCommercial – Do not use the material for commercial purposes
- NoDerivatives – Do not distribute modified versions
Full license details are available in the LICENSE file.
Legal Notice
This device is intended strictly for authorized penetration testing and security assessments. Unauthorized or illegal use is the sole responsibility of the user. Mayweather Group LLC, Practical Physical Exploitation, and its creators assume no liability for misuse or unauthorized application of this tool.