Doppelgänger Stealth
A fresh approach to an old problem

Introduction
The PPE Stealth Decoy Reader (SDR) v2 provides a novel approach to initial access and supports physical privilege escalation in badge-based environments (e.g., server rooms or restricted areas) using non-destructive methods.
What is Stealth Mode?
Stealth Mode serves two primary purposes:
- To reduce detectability in high-security areas where wireless detection measures are in place.
- To reduce power consumption by disabling the wireless access point, lowering CPU frequency, and slowing the main processing loop.
You can enable or disable Stealth Mode using the Stealth Card, which can be programmed with custom values.
Supported Card Formats
The Stealth Decoy Reader supports two distinct reader modes:
- HID Mode (Default): Supports standard Wiegand protocols and HID card formats
- Paxton Mode: Supports Paxton Net2 75-bit protocol for Paxton access control cards / fobs
Reader mode can be switched via the web interface. The device automatically configures interrupt handlers and card processing based on the selected mode.
Wiegand Formats (HID Mode)
Below are the card data formats supported in HID mode. Bit positions listed exclude parity bits, and actual implementation may vary by reader.
| Card Type | Format | Facility Code Bits | Card Number Bits | Notes |
|---|---|---|---|---|
| HID H10301 | 26-bit | 8 (1–8) | 16 (9–24) | Standard Prox |
| Indala | 26-bit | 8 (1–8) | 16 (9–25) | Requires Indala reader |
| Indala | 27-bit | 12 (1–12) | 13 (14–26) | Requires Indala reader |
| 2804 WIEGAND | 28-bit | 8 (4–11) | 14 (13–26) | Custom format |
| Indala | 29-bit | 12 (1–12) | 15 (14–28) | Requires Indala reader |
| ATS Wiegand | 30-bit | 11 (2–12) | 15 (14–28) | Custom format |
| HID ADT | 31-bit | 4 (1–4) | 23 (5–27) | ADT specific format |
| WEI32 (EM4102) | 32-bit | 15 (1–15) | 16 (16–31) | EM4102 format |
| HID D10202 | 33-bit | 7 (1–7) | 24 (8–31) | Extended format |
| HID H10306 | 34-bit | 16 (1–16) | 16 (17–32) | Extended format |
| HID Corporate 1000 | 35-bit | 12 (2–13) | 20 (14–33) | Corporate format |
| HID Simplex (S12906) | 36-bit | 8 (1–8) | 16 (19–34) | Simplex format |
| HID H10304 | 37-bit | 16 (1–16) | 19 (17–35) | Extended format |
| HID H800002 | 46-bit | 14 (1–14) | 30 (15–44) | HID H800002 format |
| HID Corporate 1000 | 48-bit | 22 (2–23) | 23 (24–46) | Extended Corp format |
| Avigilon 50-bit | 50-bit | 16 (1–16) | 32 (17–48) | Avigilon 50-bit format |
| Avigilon Avig56 | 56-bit | Configurable (N) | Configurable (54−N) | 28/28 parity; site-configurable FC/CN |
Paxton Net2 Support (Paxton Mode)
When operating in Paxton mode, the device captures and decodes Paxton Net2 75-bit protocol frames:
| Card Type | Format | Protocol | Notes |
|---|---|---|---|
| Paxton Net2 | 75-bit | Net2/EM | Native Paxton Net2 protocol capture; decodes 8-digit card numbers with parity verification |
Paxton Net2 Protocol Details:
- Card Number Extraction: 8-digit decimal card number (typically 8-9 digits)
- EM410x Conversion: Automatic conversion to EM410x hex format for card cloning
iCLASS Formats
| Card Type | Notes |
|---|---|
| iCLASS Standard | Legacy iCLASS cards |
| iCLASS SE | Secure Element cards |
| iCLASS Seos | Latest-generation secure cards |
| PIV/MF Cards | UID extraction only (UID provided in data stream) |
Additional Wiegand Features
- Keypad PIN capture (4-bit)
- Raw binary data capture
- Error detection and filtering
- Parity bit validation
Differences Between Doppelgänger Stealth and Core
The primary difference between the Stealth and Core firmware lies in their wireless access point functionality, which reflects the intended use case and operational environment for each device.
-
Doppelgänger Stealth is designed to be placed in a stationary location while the operator remains out of sight—or entirely off-site. For this purpose, Stealth operates as a wireless access point. You can also disable the access point entirely using the Stealth Card, which is ideal for high-security environments where wireless detection controls may flag rogue or unauthorized networks.
-
Doppelgänger Core is intended for use with long-range readers, where the operator needs to maintain persistent communication or where multiple operators require access to the device’s web interface. Core also supports email notifications and haptic feedback triggers, eliminating the need for the operator to constantly refresh the web application to check for successful card reads.
Initial Setup Instructions
To get started, simply slide the power switch to the ON position (to the left) and connect to the access point doppelgänger_XXXX (default password: UndertheRadar).
Change Wireless Credentials
It is highly recommended to change the default wireless credentials. To do this, navigate to the Configuration Page and click the Modify Wireless Network button.
Stealth Card
The device supports separate stealth card configurations for HID and Paxton modes. We recommend configuring the Stealth Card with custom values.
HID Stealth Card (Default):
| Bit Length | Facility Code | Card Number |
|---|---|---|
| 26 | 222 | 1337 |
Custom HID Stealth Card values must fall within the following ranges:
| Bit Length | Facility Code | Card Number |
|---|---|---|
| 26 or 35 | 1–255 | 1–65,535 |
Paxton Stealth Card:
| Hex Value |
|---|
| 0000001337 |
The device is mode-aware and will check the appropriate stealth card based on the current reader mode (HID or Paxton).
Reader Mode Selection
The device supports switching between HID and Paxton reader modes:
- Navigate to the Configuration Page
- Select “HID Global” or “Paxton” from the reader type dropdown
- The device will automatically reconfigure interrupt handlers and card processing
Mode-Specific Behavior:
- HID Mode: Processes standard Wiegand protocols (26-bit through 56-bit formats)
- Paxton Mode: Captures Paxton Net2 75-bit protocol frames with automatic decoding
Serial Debugging
For OPSEC purposes, you can enable or disable serial output over the USB-C connection. To modify this behavior, navigate to the Configuration Page.
Resetting the Device
To reset the device, navigate to the RESET page. Here you will have several options available. Select the desired button. In some cases the device will recycle power (e.g., Full Device Reset, Wireless Credentials).
Writing Captured Card Data
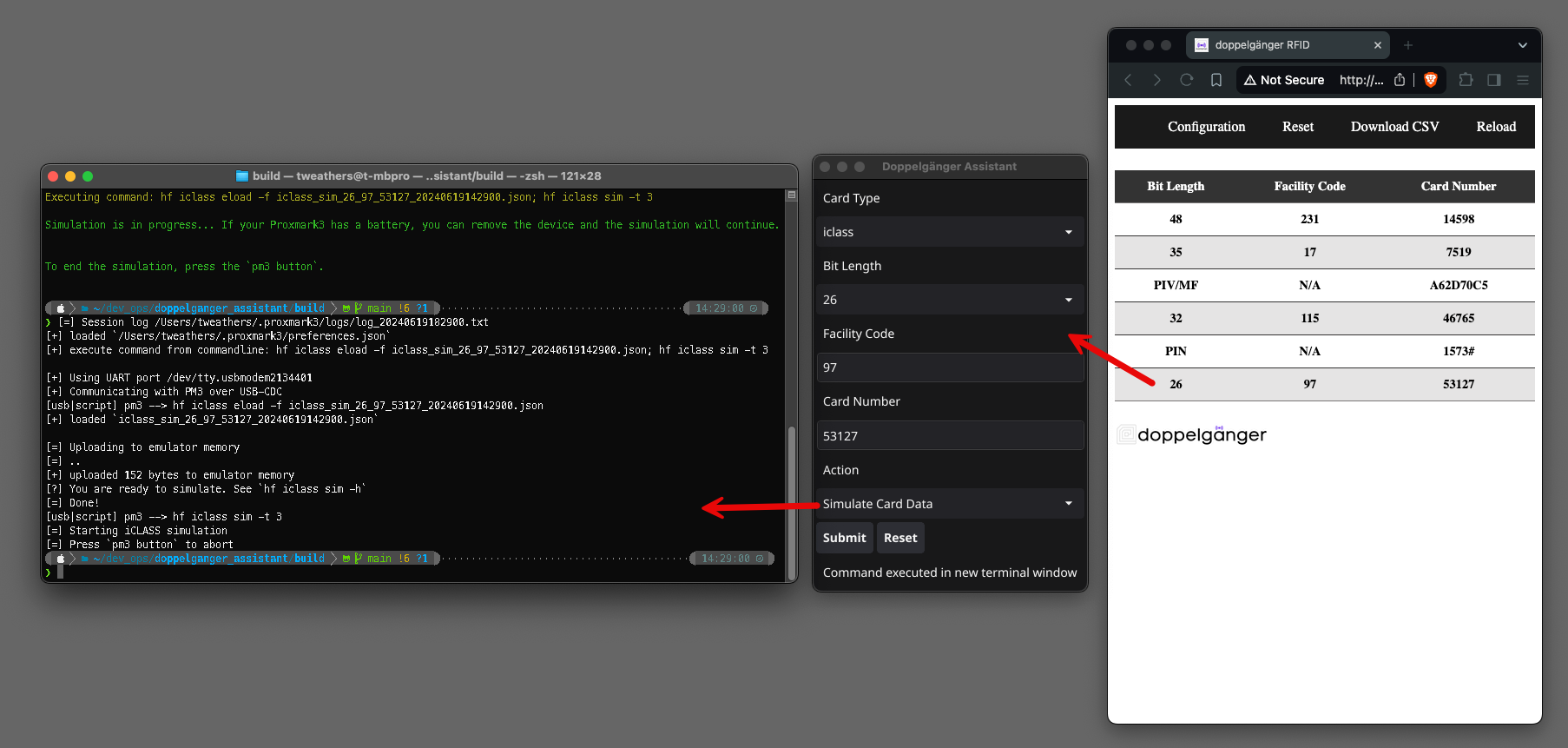
To efficiently manage and write captured RFID data, use the official Doppelgänger Assistant application. This tool simplifies generating Proxmark3 commands, writing data to blank RFID cards, and simulating captured card data. Doppelgänger Assistant supports macOS, Linux, and Windows (via WSL).
License Information
This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
You are free to:
- Share – Copy and redistribute the material in any medium or format
Under these terms:
- Attribution – Provide appropriate credit, a link to the license, and indicate if changes were made
- NonCommercial – Do not use the material for commercial purposes
- NoDerivatives – Do not distribute modified versions
Full license details are available in the LICENSE file.
Legal Notice
This device is intended strictly for authorized penetration testing and security assessments. Unauthorized or illegal use is the sole responsibility of the user. Mayweather Group LLC, Practical Physical Exploitation, and its creators assume no liability for misuse or unauthorized application of this tool.